Look quickly! What should I do if there is a virus in my computer?
What is a computer virus?
Computer virus is a malicious program, whose purpose and function is to destroy the computer system, so that the computer can not be used normally, or even destroy software and hardware resources and delete user data, until the system crashes.
What is a Trojan horse?
Trojan horse is a special computer virus. Besides the universality of the virus, such as transmission, concealment, infectivity and latency, its biggest feature is that it can be controlled remotely. That is, hackers can use trojans to remotely control and operate computers implanted with Trojan viruses, so as to achieve the purpose of destroying and stealing information from inside. This feature is the origin of its name-this virus, like a Trojan horse in ancient Greek mythology, sneaks into the enemy’s interior, can accept external instructions, and does damage from the inside out.
"infected with computer virus"
Typical cases leading to leaks.
Case 1
Tang, a staff member of a unit, illegally connected a classified laptop to the Internet and was remotely implanted with a Trojan virus. After technical appraisal, dozens of confidential documents were stolen, which caused serious damage to national security interests. Tang’s behavior constituted a crime of negligent disclosure of state secrets, and he was sentenced to 2 years and 5 months in prison according to law. The relevant personnel with major leadership responsibilities in the unit were severely warned by the party and given administrative demerits.
travel to watch industry
Sun, a senior engineer of a military industrial group, collected many technical documents and materials from the Internet when compiling the project plan. Because of the special field of this data, it attracted the attention of overseas intelligence agencies and sent a Trojan stealing program to their Internet computers. Without knowing it, Sun copied the relevant information and the hidden Trojan stealing program into the USB flash drive, then connected the USB flash drive to the classified computer and imported the file. Repeatedly, the Trojan stealing program hides the files and data in the computer in the U disk, and transmits them when connecting with the Internet, resulting in the theft of many confidential files. After the incident, Sun was dismissed from public office.
Relevant laws and regulations
Article 48 (8) of the Secrecy Law stipulates that those who connect classified computers and classified storage devices to the Internet and other public information networks shall be punished according to law; If a crime is constituted, criminal responsibility shall be investigated according to law.
Article 48 (9) of the Secrecy Law stipulates that those who exchange information between classified information systems and the Internet and other public information networks without taking protective measures shall be punished according to law; If a crime is constituted, criminal responsibility shall be investigated according to law.
What measures are there to prevent computer viruses?
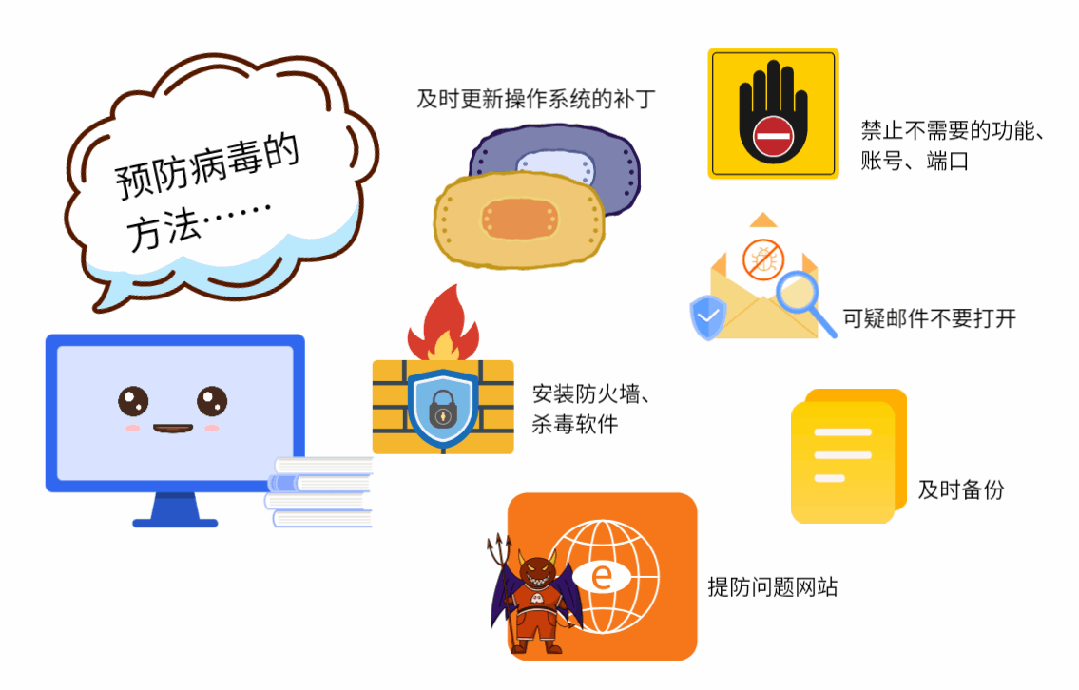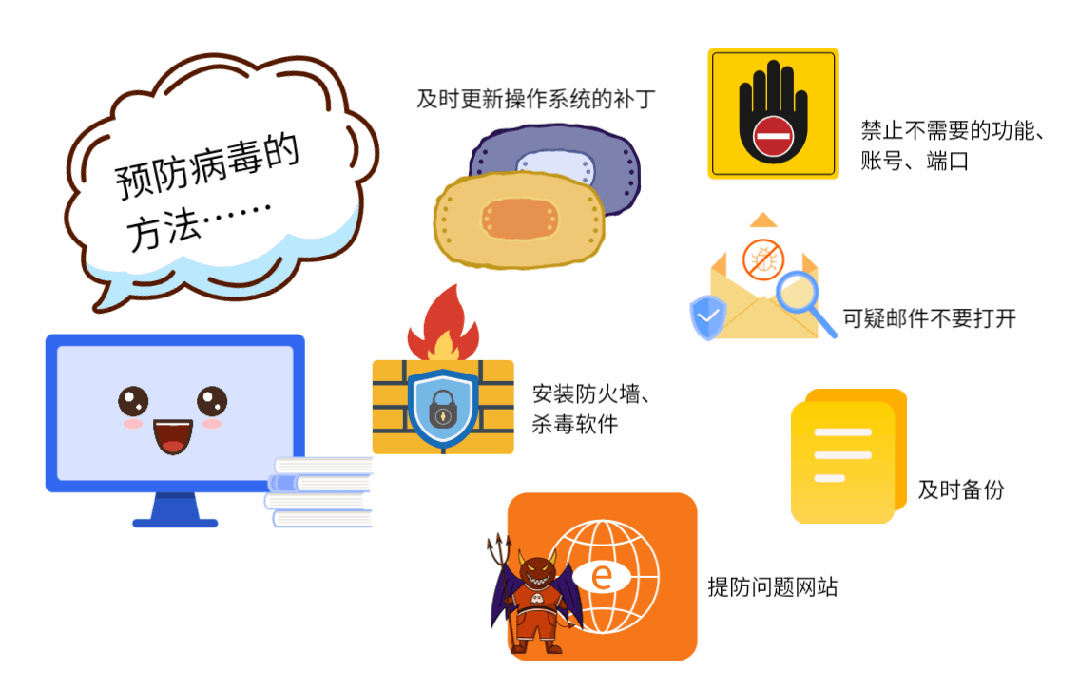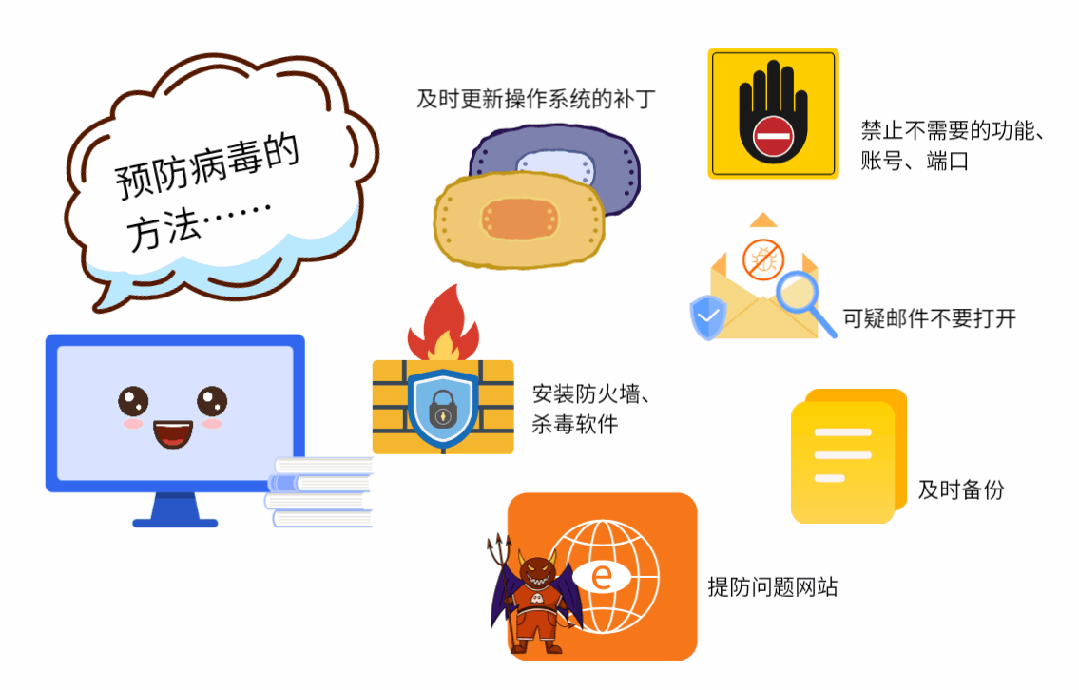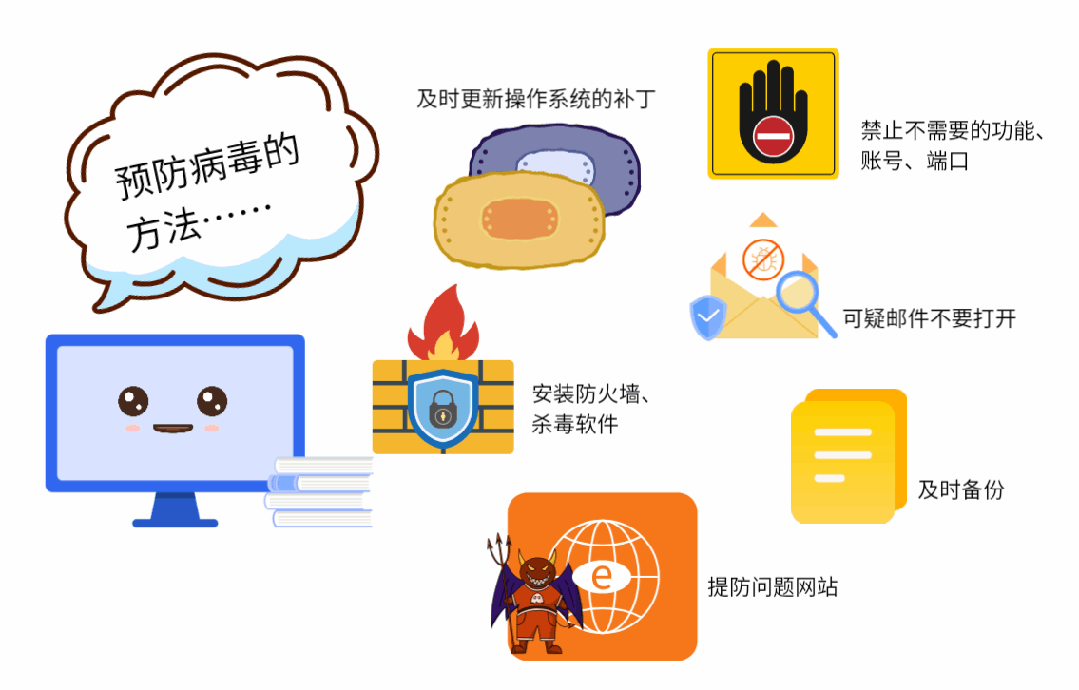
(1) Update the operating system patch in time.
(2) Disable unnecessary functions, accounts and ports.
(3) Install protection software, such as firewall, antivirus software and intrusion detection software.
(4) Beware of problematic websites to prevent being implanted with Trojans or infected with viruses.
(5) When receiving strange and suspicious emails, try not to open them, and disinfect them before opening them.
(6) For important documents and data, make regular backups to avoid loss.
What should I do if there is a virus in the computer?
(1) Disconnect the network connection. Quickly unplug the network cable or turn off the router to reduce the possibility of information leakage and virus spread.
(2) Back up important files. If the computer can still run, you should back up important files to the U disk or mobile hard disk as soon as possible to avoid accidental killing or deletion of important files by antivirus software.
(3) killing viruses. It’s best to find professionals to use special tools. If you can’t get support for the time being, you should use antivirus software from different manufacturers, that is, at least two or more tools should be used for cross-cleaning.
(4) Reinstall the system and modify the password. After restoring the system, you should immediately change the computer and network-related passwords to prevent illegal users from logging in to the computer again, causing unnecessary losses.
Source: Easy Learning Security: Computer and Network, Shenzhen Security.


How much do you know about the hidden dangers of leaks around you? Be alert! Don’t let social media become a "high-risk place" for leaks. Be careful! This kind of photo may reveal state secrets! For more exciting information, please pay attention:
Official WeChat of Fuyu Cooperation Zone: FYICP2019
Official Weibo of Fuyan Cooperation Zone: @ Fuyan Industrial Cooperation Zone
Submission/suggestion: fuyanhezuoqu@163.com continues to slide to see the next one.
Look quickly! What should I do if there is a virus in my computer? Touch and read the original text in Fuyan Cooperation Zone.
Original title: "Look quickly! What should I do if there is a virus in my computer? 》
Read the original text